The scammers and hackers in the cryptocurrencyA digital currency running on a blockchain and built with cryptography. Contrary to central-bank issued currency, cryptocurrency issuance rules are... More world never sleep. Now, they’ve designed a campaign of fake ransomware to extort bloggers and website owners. Specifically, they’re affecting WordPress sites, and asking 0.1 BTCAn abbreviation for Bitcoin. to the owners if they want them back. The trick is there’s no real threat ongoing, despite the sudden announcement that appears.
In a real infection with ransomware (a type of malware), the files, website, and/or the entire disk are encrypted by hackers remotely. In order to give them back safely, the cybercriminals ask for a monetary ransom, usually in cryptocurrencies. This is informed by a sudden announcement that appears on the whole screen, blocking all the functions.
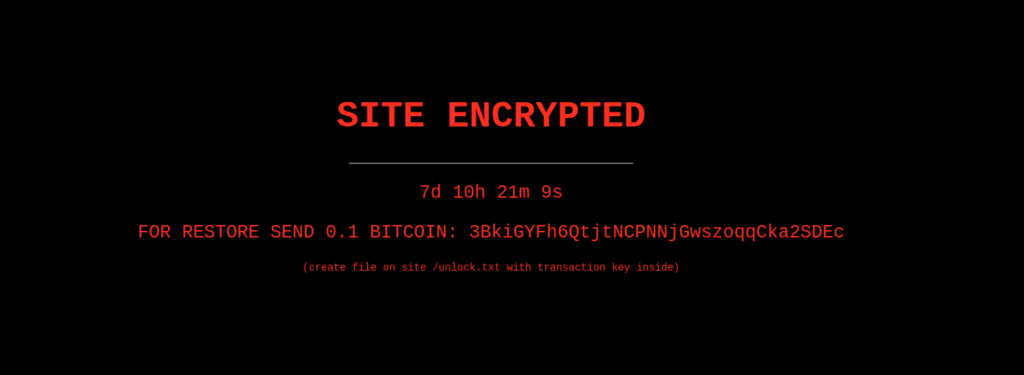
In this case, as it was described by the firm Sucuri, the classic ransomware announcement is also there. It says in bright red that the website is encrypted, it has a countdown, and asks for 0.1 BTC (around $6,000) to be sent to a specific addressAn address is a blockchain equivalent to a bank account number in the traditional financial system, or an email address.... More. However, all this is barely smoke and mirrors. The researchers discovered that this ransomware is fake, and it’s only a malicious plugin to deceive the website owners.
What this plugin does is return all the published posts to draft, while blocking the screen with the fake ransomware announcement. That’s something easily solvable by removing the plugin manually and running a command to republish the posts and pages. The main objective of the hackers was never to encrypt the files, but to scare the owners enough to make them pay the ransom.
Luckily, it seems that no one has fallen so far. The Bitcoin address indicated in the announcement still has zero funds.
Ways to get fake ransomware
In this case, Sucuri found out that the source of the plugin was the wp-admin panel itself. This means that the hackers had administrator access to the websites. They could have entered by brute-forcing the password (using software to repeatedly try to figure out the password). Although, since the attack is being held on so many sites (almost 300), it’s more likely that they took previously leaked passwords from the Darknet.

The malware, in general, is usually distributedA distributed system is made of components that are running on different networked computers, which communicate and coordinate their actions... More by email, or by deceiving the victims somehow. This way isn’t very common, but there are some things we can do to protect our sites and devices from fake ransomware and everything else. In the first place, to check if your password hasn’t been previously stolen, you can consult sites like Have I Been Pwned. Domain, email, and phone searches are also available there.
It’s also important to have some basic security measures, like changing passwords after some reasonable period. Download files and software only from the official sites, and check twice the URLs to be sure. Likewise, it’s important to keep updated the OS, antivirus, and firmware of all your smart devices, and don’t open links or attached files from dubious emails. Finally, in case that the worst happens, a solid backup of all data will be of great help.
Featured Image by Yuri Samoilov / Flickr
Wanna trade BitcoinBitcoin is the first decentralized digital currency. It was created in 2009, by an anonymous founder or group of founders... More and other tokens? You can do it safely on Alfacash! And not forget we’re talking about this and a lot of other things on our social media.
Twitter * Telegram * Facebook * Instagram * Youtube * Vkontakte








